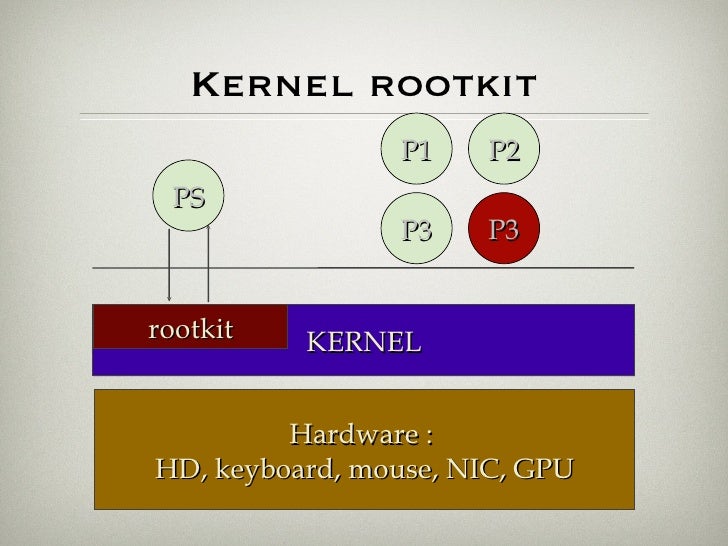
Rootkit Ntoskrnl Executive Branch
The phrases below describe fields in a firewall rule. Match the field with its description. ___ Numbers the rules for cross-referencing purposes ___ Is either Allow or Deny ___ Is either In for inbound traffic or Out for outbound traffic ___ Is either TCP, UDP, or Any ___ Identifies the host and service that produced the packet ___ Identifies the host and service intended to receive the packet ___ Is the number of the corresponding statement in a security policy A. Destination socket B. Policy number D. Source socket E.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Sed risus augue, dignissim sit amet est sit amet, tincidunt lobortis nunc. Nulla facilisi. Fusce a libero at nunc feugiat tincidunt. Vestibulum a quam et tellus interdum molestie nec. Evolution 123 A Street San Francisco, CA 38279. Email: company@mycompany.com. Review for final. (FISMA) requires U.S. Executive branch agencies to. A rootkit is: A. Software that.
Control number F. Transport protocol. The phrases below describe common types of malware propagation techniques. Match the technique with its description.
___ Copies itself to external flash drive, then configures drive to execute malware when drive is inserted into a computer ___ User visits a web page or clicks on a pop-up window, unintentionally transferring malware to the user's computer ___Exploits a computer vulnerability to install itself and replicate across a network ___ Appears benign but contains malware; tricks user into executing the infected file ___ Arrives via email; the user executes the malware from e-mail and infects computer A. Worm propagation B. Infect USB drives C. Email infection D. Drive-by download E. Trojan infection. _B__ Copies itself to external flash drive, then configures drive to execute malware when drive is inserted into a computer _D__ User visits a web page or clicks on a pop-up window, unintentionally transferring malware to the user's computer _A__Exploits a computer vulnerability to install itself and replicate across a network _E__ Appears benign but contains malware; tricks user into executing the infected file _C__ Arrives via email; the user executes the malware from e-mail and infects computer.
Identify three of these: 1. Bara No Sabaku Drama Cd R18 on this page. Each statement uses the word 'shall' unless the policy statement is optional. There should be a way to test the implementation to determine if the policy statement is true. The policy provides a list of features to be tested. Each statement identifies which prioritized risks the statement is intended to address. Whenever possible, phrase the statements in a positive and specific sense. Policy statements should describe what the system does, instead of talking about what it doesn't do.
[root &windows ] #volatility -f Win7.bin --profile=Win7SP0x86 gdt Volatility Foundation Volatility Framework 2.4 CPU Sel Base Limit Type DPL Gr Pr ------ ---------- ---------- ---------- -------------- ------ ---- ---- 0 0x0 0x00000000 0x00000000 0 By Np 0 0x8 0x00000000 0xffffffff Code RE Ac 0 Pg P 0 0x10 0x00000000 0xffffffff Data RW Ac 0 Pg P 0 0x18 0x00000000 0xffffffff Code RE Ac 3 Pg P 0 0x20 0x00000000 0xffffffff Data RW Ac 3 Pg P 0 0x28 0x801db000 0x000020ab TSS32 Busy 0 By P 0 0x30 0x8292ec00 0x00003748 Data RW Ac 0 By P.